OPEN-SOURCE SCRIPT
HTF High/Low Repaint Strategy
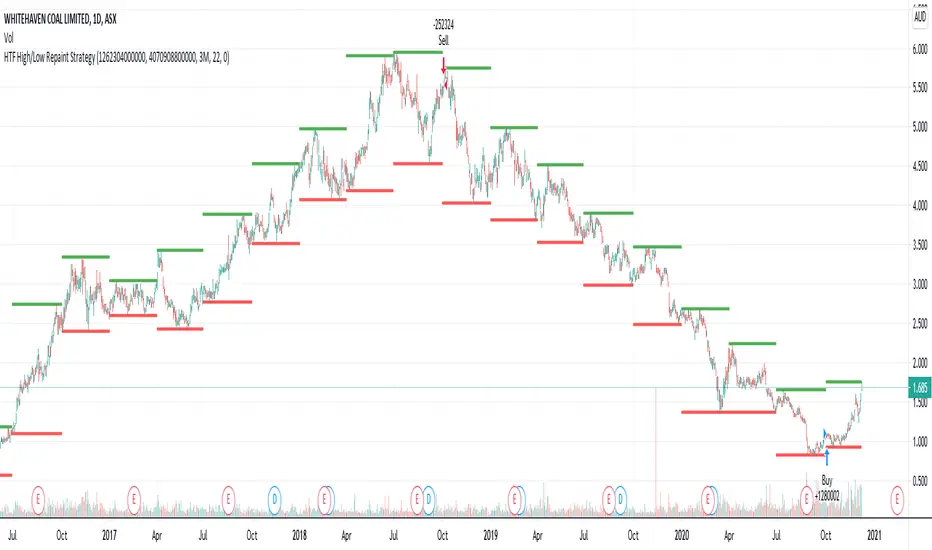
Here is an another attempt to demonstrate repainting and how to avoid them. It happened few times to me that I develop a strategy which is giving immense returns - only to realize after few forward testing that it is repainting. Sometimes, it is well disguised even during forward testing.
In this simple strategy, conditions are as below:
Buy : When a 3M bar produces high and low higher than it's previous 3M bar high, low
Sell : When a 3M bar produces high and low lower than its previous 3M bar high, low.
Default setting is : lookahead = on and offset = 0
This means current 3M bar high low is plotted for all the daily bars within this month. Which means, strategy looks ahead of time to see this 3M bar high is higher than previous 3M bar high during the start of the first daily bar. Hence, this combination leads to massive repaint.
For example, trade made on October 2nd 2018 already knows well ahead of time that price is going to go down in next 3 months:

Similarly, after 2 years on October 2nd 2020 - the strategy already knows that last 3M high is going to be breached on 7th December 2020

Solution: If you are using security for higher timeframes, safer option is always to use offset 1. Further details in the trading view script:

BUT
It may still repaint if we are passing function to security.
For example:
f_secureSecurity(_symbol, _res, _src) => security(_symbol, _res, _src[1], lookahead = barmerge.lookahead
This function will likely avoid any repainting with Higher timeframe if we are passing in built variables such as high, low, close, open etc. But, if we try to pass supertrend, this will not produce right results. This is because supertrend calculation in turn uses high/low/close values which do not consider the offset while calculating. Hence, even with offset 1, this will still produce issues.
Hence, the call:
[supertrend, dir] = f_secureSecurity(syminfo.tickerid, derivedResolution, supertrend(3,10), offset) will again lead to massive repainting. Solution to this is to implement supertrend function and use high, low, close values derived from secureSecurity.
Quick tips to identify or be suspicious about repainting
If these things happen, be wary about repainting and do a through check of all security function usage in your strategy.
All the best :)
PS: Apply 3-5 days resolution and see the fun. Also, WHC is one hell of a Christmas tree. Could have made immense profit in the same strategy even without repainting.
WHC is one hell of a Christmas tree. Could have made immense profit in the same strategy even without repainting.
In this simple strategy, conditions are as below:
Buy : When a 3M bar produces high and low higher than it's previous 3M bar high, low
Sell : When a 3M bar produces high and low lower than its previous 3M bar high, low.
Default setting is : lookahead = on and offset = 0
This means current 3M bar high low is plotted for all the daily bars within this month. Which means, strategy looks ahead of time to see this 3M bar high is higher than previous 3M bar high during the start of the first daily bar. Hence, this combination leads to massive repaint.
For example, trade made on October 2nd 2018 already knows well ahead of time that price is going to go down in next 3 months:
Similarly, after 2 years on October 2nd 2020 - the strategy already knows that last 3M high is going to be breached on 7th December 2020
Solution: If you are using security for higher timeframes, safer option is always to use offset 1. Further details in the trading view script:

BUT
It may still repaint if we are passing function to security.
For example:
f_secureSecurity(_symbol, _res, _src) => security(_symbol, _res, _src[1], lookahead = barmerge.lookahead
This function will likely avoid any repainting with Higher timeframe if we are passing in built variables such as high, low, close, open etc. But, if we try to pass supertrend, this will not produce right results. This is because supertrend calculation in turn uses high/low/close values which do not consider the offset while calculating. Hence, even with offset 1, this will still produce issues.
Hence, the call:
[supertrend, dir] = f_secureSecurity(syminfo.tickerid, derivedResolution, supertrend(3,10), offset) will again lead to massive repainting. Solution to this is to implement supertrend function and use high, low, close values derived from secureSecurity.
Quick tips to identify or be suspicious about repainting
- Unbelievable results on all timeframes and all instruments with both long and short trades
- Lower timeframes giving significantly higher returns on backtest when compared to higher timeframe
If these things happen, be wary about repainting and do a through check of all security function usage in your strategy.
All the best :)
PS: Apply 3-5 days resolution and see the fun. Also,
Open-source Skript
Ganz im Sinne von TradingView hat dieser Autor sein/ihr Script als Open-Source veröffentlicht. Auf diese Weise können nun auch andere Trader das Script rezensieren und die Funktionalität überprüfen. Vielen Dank an den Autor! Sie können das Script kostenlos verwenden, aber eine Wiederveröffentlichung des Codes unterliegt unseren Hausregeln.
Trial - trendoscope.io/trial
Subscribe - trendoscope.io/pricing
Blog - docs.trendoscope.io
Subscribe - trendoscope.io/pricing
Blog - docs.trendoscope.io
Haftungsausschluss
Die Informationen und Veröffentlichungen sind nicht als Finanz-, Anlage-, Handels- oder andere Arten von Ratschlägen oder Empfehlungen gedacht, die von TradingView bereitgestellt oder gebilligt werden, und stellen diese nicht dar. Lesen Sie mehr in den Nutzungsbedingungen.
Open-source Skript
Ganz im Sinne von TradingView hat dieser Autor sein/ihr Script als Open-Source veröffentlicht. Auf diese Weise können nun auch andere Trader das Script rezensieren und die Funktionalität überprüfen. Vielen Dank an den Autor! Sie können das Script kostenlos verwenden, aber eine Wiederveröffentlichung des Codes unterliegt unseren Hausregeln.
Trial - trendoscope.io/trial
Subscribe - trendoscope.io/pricing
Blog - docs.trendoscope.io
Subscribe - trendoscope.io/pricing
Blog - docs.trendoscope.io
Haftungsausschluss
Die Informationen und Veröffentlichungen sind nicht als Finanz-, Anlage-, Handels- oder andere Arten von Ratschlägen oder Empfehlungen gedacht, die von TradingView bereitgestellt oder gebilligt werden, und stellen diese nicht dar. Lesen Sie mehr in den Nutzungsbedingungen.